On Tuesday May 31st we’re going to change the categories on this blog, so if by any chance you’re using a feed of a specific category, that’s going to break. We suggest subscribing to the whole blog for maximum enjoyment! If you’re not a LIS staff member & would like to filter out the more staff related posts, you can subscribe to the new “Middlebury Community Interest” category after May 31st. The other categories will be “LIS Staff Interest”, and “Post for MiddPoints” which will cause the post to be added to the MiddPoints blog too. All the old categories except “The Essentials” will be converted to tags for easy searching.
The LIS Web team developed this new scheme, following recommendations that came out of the open meeting about the future of the LIS Blog (including a call for simplified categories). The AD Team reviewed and approved these changes. We welcome your comments.
Tag Archives: Security
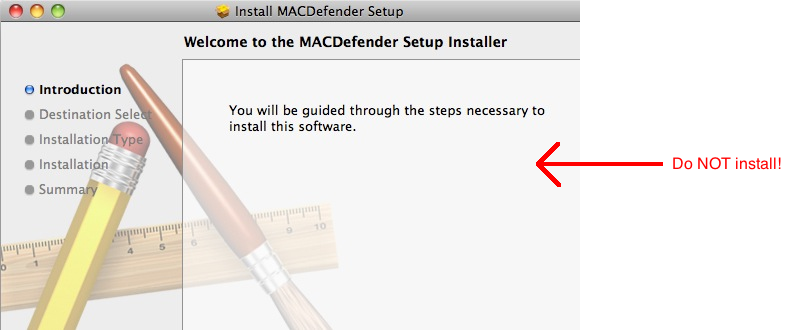
Do Macs get viruses? (or “Just say NO to MACDefender”).
Viruses on Macs? You don’t say!
The Helpdesk is occasionally confronted with this question: Do Macs get viruses? The short answer is yes, they do. Actually, there are quite a few viruses, worms and trojans that target Macs (see the iAntivirus Threat Database). That’s why we offer antivirus software for Macs: http://go.middlebury.edu/sav. Note that Symantec has been included on faculty/staff computers for several years. It’s also offered to all students (though we might not do a good job advertising that).
What’s MACDefender?
Recently, a new malicious software has been targeting Macs (SANS, Symantec, Cornell). The software is (deceptively) named MACDefender. Strictly speaking, MACDefender is not a virus, it is a trojan but for most people there is purely a semantic difference. It should be noted, however, that a computer trojan, much like its historical counterpart, relies on deception and requires our “help” to infiltrate a computer. Computer viruses and worms on the other side don’t depend, as much, on us humans.
How do you know if your computer has been infected with MACDefender?
Well, at this time, if your computer is infected with MACDefender you may see the symptoms outlined on the Intego antivirus page. However, a better approach would be to update your real Mac antivirus (you have one, right?) Here are the instructions for updating Symantec Antivirus for Mac and running a virus scan. Don’t have Symantec for your Mac? Get it now: http://go.middlebury.edu/sav.
Two new staff in Central Systems & Network Services
Please welcome two new staff members in CSNS:
- Ian Burke started November 29th as our new Network Security Administrator; he is also on the LIS Security Team. Ian comes most recently from Amherst, NH and was a Security Engineer for TJX in Framingham MA.
- Jim Stuart started December 8th as System Programmer/Administrator. Jim was Chief Technology Officer for Qvault, Inc. here in Vermont. He previously worked here at Middlebury from 1993-1999 in various positions in ITS, prior to the merger which created LIS.
Illegal File Sharing and the Higher Education Opportunity Act
In April 2008 the Department of Education drafted the Higher Education Opportunity Act (HEOA). HEOA deals with unauthorized file sharing on campus networks and enforcement of this act’s provisions began July 1, 2010. Institutions of higher education must make an effort to comply with the provisions of this act. The Educause website provides an excellent overview of the provisions of the act, as well as suggestions for complying. Here’s a relevant excerpt from Educause’s site:
Several sections of the HEOA deal with unauthorized file sharing on campus networks, imposing three general requirements on all U.S. colleges and universities:
- An annual disclosure to students describing copyright law and campus policies related to violating copyright law.
- A plan to “effectively combat the unauthorized distribution of copyrighted materials” by users of its network, including “the use of one or more technology-based deterrents”.
- A plan to “offer alternatives http://www.educause.edu/legalcontent to illegal downloading.”
To comply with the act, Middlebury College has undertaken the following steps:
- Legal alternatives to illegal downloading are described in the Computing Policies section of the handbook: go.middlebury.edu/p2p
- Copyright laws and policies are published through Middlebury College’s copyright page (go.middlebury.edu/copyright), as well as the Computing Policies section of the Handbook, in particular go.middlebury.edu/p2p
- A plan is in place to combat unauthorized distribution of copyrighted materials. The plan relies on a combination of packet shaping and NAC technology, as well as education:
- Every year, students register their computing devices through our network registration process. Part of the registration involves reading and agreeing to our Responsible Use policy. Network registration is enforced through a NAC appliance from Bradford networks.
- We respond promptly and regularly to DMCA notices. The College has a DMCA agent that promptly contacts the user that is in violation according to the DMCA notice. Repeated offenses result in loss of network access.
- The use of posters that regularly appear in commonly used public spaces, such as the Davis Family Library.
- This plan is reviewed periodically through the work of the security team.
Note that Educause offers a selection of Role Model Institutions that have implemented a variety of similar compliance strategies.
You must be logged in to post a comment.