From September 15th thru October 15th, the United States celebrates Hispanic American / Latinx Heritage Month. Read below to find out how some of the people at Midd engage with these identities. Also come by the Davis Family Library September 18th-29th to see the display. Many sincere thanks to Marlena Evans 🙂 for her committed work in developing banner designs.
Names of Respondents; Hometowns; Roles on Campus:

Zarai Zaragoza, a Mexican American Middlebury College senior and studio art major sits in front of colorful art pieces.
ZZ: Zarai Zaragoza; Chicago, Illinois; Studio Art Major with Education Studies Minor – Part of Alianza, WOC [Women of Color], DMC [Distinguished Men of Color], Anderson Freeman Center Fellow, and so much more.
MRM: Marcos Rohena-Madrazo; San Juan, Puerto Rico; Assistant Professor of Spanish / Linguistics.
KS: Katrina Spencer; Los Angeles, California; Literatures & Cultures Librarian.
XM: Ximena Mejía; Salisbury, Vermont; Middlebury College Counseling Director.
Time at Midd:

Middlebury College Assistant Professor of Spanish and Linguistics Marcos Rohena-Madrazo, born and raised in Puerto Rico, poses for a photo at the Davis Family Library Research Desk.
ZZ: 3 years, going on the 4th.
MRM: 6 years.
KS: 7.5 months.
XM: 9 years.
What do you know about Hispanic American/Latinx Heritage Month?
ZZ: Hispanic Heritage month celebrates the histories, cultures and contributions of American citizens whose ancestors came from Spain, Mexico, the Caribbean and Central and South America. It is a time to show the love one has for their culture, traditions, and the many identities that make up the Hispanic community.
MRM: I don’t know a lot about the month, per se, but I know that it’s important in the United States context and I’ve been learning more about it since I’ve lived “here” [on the mainland and not the island of Puerto Rico]. When I was living in Puerto Rico, there wasn’t a need to actively identify with either of those labels. Only recently have I started to engage with them.

Literatures and Cultures Librarian Katrina Spencer, whose father is Afro-Costa Rican, poses in her office while preparing books for the Hispanic American/Latinx Heritage Month display.
KS: Unlike many other commemorative months, this one starts in the middle of September and ends in the middle of October. These dates were chosen in remembrance of a variety of Latin American countries winning their independence from colonial powers.
XM: It commemorates the diversity of the identities that encompass “Hispanic” and Latinx.
How do you pronounce “Latinx” and what does it mean?
MRM: In English, [lə.ˈthi.ˌnɛks]. In Spanish, I’m not sure because grammatical gender is much more complex. I’m still figuring it out. For me, it means a person of Latin American descent in/from a U.S. context.
KS: La-teen-x. Three syllables. You pronounce the “x” just like the letter “x.” To my understanding, the “x” is meant to draw attention away from gender specificity. In Spanish, grammatically speaking, the default term is “Latino,” an adjective that inherently prioritizes the masculine and invisibilizes the feminine. The “x” is an attempt to acknowledge the ways in which language, depending upon how we use it, can be inclusive or exclusive.
XM: Well said Katrina! Breaking down the gender binary.

Middlebury College Counseling Director Ximena Mejía, of Ecuadoran and European ancestry, poses for a photo.
ZZ: Laa-Tee-Nex. I love the way Katrina describes it. It is meant to be more inclusive since the Spanish language is structured to be more gendered.
How do you identify ethnically?
ZZ: Both of my parents are from Guerrero, Mexico. I was born in the U.S, but am very connected to the traditions of my cultural. I am Mexican-American → Latina.
MRM: Puerto Rican. If there is one identity that I can unproblematically claim, it is Puerto Rican. Where were my ancestors “from”? On my mom’s side from Cantabria and Mallorca and on my dad’s side general Caribbean Afro-Euro combo.
KS: My mother is African American and Creole; my father is Afro-Costa Rican. So. . . I’m black. 😉 With some cultural, historical and social connections to both Central America and the Caribbean, broadly defined. Not one of these, however, for me, is an “ethnicity.” (Or are they?)
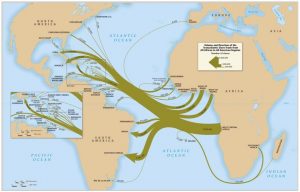
A map depicting the many departures from the African continent and arrivals to the “New World.” The image is taken from David Eltis’ Atlas of the Transatlantic Slave Trade, on display now in the Davis Family Library. See the circular information desk.
XM: Multiethnic / Mestiza a combination of North Ecuadorean indigenous people and European (German and French from maternal side and Spanish from paternal side).
Why is it important to have a display to commemorate this month?
ZZ: It’s a beautiful thing to take pride in your culture, your family’s culture, and how these traditions, stories, and art impact your interests and your sense of self. It’s very important to give identities that are sometimes overlooked, ignored, or marginalized, some space of confidence, openness, and growth. Speaking from experience, it is not always easy to take pride in one’s apparent (sometimes not apparent) identity, and it can often be thrown in your face that you’re different. I am hoping that this display will show differences but will shine it in a positive, wholesome light.

The cover of Pulitzer Prize winning author Junot Díaz’s 2012 book This Is How You Lose Her is depicted here. His work regularly engages what it means to be both Dominican and American.
MRM: It’s important in order to counter hegemonic discourses of who the people living in the United States are.
KS: I want more students of diverse and non-dominant/non-hegemonic backgrounds to know what materials we have in our collections that mirror their experiences, lives, and struggles. If we don’t highlight them, they may never know that they’re there. The library is theirs, too.
XM: Make visible to our larger community that there are students, faculty and staff who identify with this heritage.
What are some of the challenges in preparing a display such as this?
ZZ: Often times there can be an misrepresentation of a group of people. What I hope this display will do is bring together a true, multifaceted array of stories, backgrounds, and talents that make up the Hispanic community at Midd.
MRM: Choosing who and what to represent. It’s by no means a unified and easily portrayable group.
KS: “Who is Hispanic?” “Who is Latinx?” “Who is not?” For example, do we include Brazil and Brazilians? And how? How do we include works that represent all of them? Are all my choices generational and based on what I liked growing up? Will students even recognize these items I’ve chosen?

The cover art for 2013 Venezuelan feature-length film Pelo Malo (Bad Hair) is pictured here.
What readings/music CDs/DVDs might you recommend that your peers check out to commemorate this month?
ZZ: Recently… Latinoamerica by Calle 13 has been my jam, my motivator, my sense of pride. Give it a listen, look at the music video if you can. Internacionales by Bomba Estereo is also a great tune!
MRM: Junot Díaz. Rita Indiana ‘cause she’s got diaspora all over the place. Daddy Yankee. That’s very Caribbean, but that’s my experience. Ooh, ooh, also Brujos — queer-of-color geekstravaganza!
KS: All things Junot Díaz. Contemporarily, he’s likely the most famous writer who represents the Hispanophone world transnationally. Also Achy Obejas, writes on themes touching the queer Latina world. I’ve been wanting to see Pelo Malo (Bad Hair) for quite some time. We have it in the library on Bluray. I believe it studies hair straightening, a practice that often favors western European features, a discourse that continues to be relevant in the Afro-Latinx world today.
XM: Music: Bomba Estereo, Los Cojolites, Gina Chavez, Perota Chingo, Calle 13, Manu Chao, Cultura Profetica, Onda Vaga.
Books: Umami by Laia Jufresa; Juliet Takes a Breath by Gabby Rivera; Multiple Choice by Alejandro Zambra; Bruja by Wendy C. Ortiz; Transmigration of Bodies by Yuri Herrera; Among Strange Victims by Daniel Saldaña Paris, and more.
Anything else?
MRM: The more we talk about what “Latinx” is and what it isn’t, the more we understand ourselves and each other.

A screenshot taken from a Pero Like video of producer Julissa Calderón who often discusses her Dominican heritage in her work.
KS: There’s an Afro-Dominican actress and filmmaker, Julissa Calderón, regularly featured on Pero Like and a comedian and filmmaker who’s black and Honduran who produces content on “Callme Choko.” Aside from being hilarious dramatists, they both give greater representation to minority populations that too often go unseen.
ZZ: Thank you for providing the space… <3
If there’s a work you’re interested in seeing and feel the library should own, visit go.middlebury.edu/requests to let us know!