To help raise awareness about community efforts to prevent significant security issues, Middlebury Information Security has launched a ‘Security Scout of the Month’ award.
Highlighting the valuable contributions of community security scouts in an @MiddInfoSec blog post and on Middlebury’s Information Security web site is a great way to show how a cautious and thoughtful approach to computing can protect the College community from cyber risks.
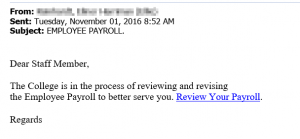
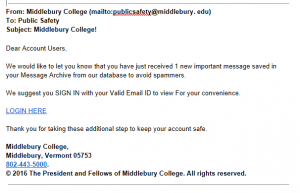
As an example, this past month, an attack against Middlebury’s Banner system was avoided thanks to the contributions of an astute member of our community, Justin Allen, who spotted a targeted phishing attack and raised the awareness around this malicious event.
As Justin Allen describes it:
“I received an email that started out dear account owner which usually gets my attention and as I read down thru the email I noticed that it said I had signed up for a paperless W-2 which I did not and it wanted me to logon to view it. After that I noticed a couple of another things that did not make sense for my Middlebury account one was the sender of the email which wasn’t from the college at all and we all have been told time and time again if the address doesn’t end with middlebury.edu it’s not from the college. Below is a copy of what was sent to me.”
This astute awareness is why Justin is this month’s ‘Security Scout of the Month’.
We are excited to celebrate the hard work and security conscious efforts of our community. Please watch for the next ‘Security Scout of the Month’ and help us recognize these efforts.
If you would like to recognize an individual for their information security contributions or would like to raise an information security concern, please contact infosec@middlebury.edu.