The US began looking into North Korea’s computer network in 2010, reports claim
Category Archives: Cyberwarfare
US (Sort of) Points to “Smoking Gun” Linking North Korea to Sony Hack
Citing anonymous sources in and close to the US government, The New York Times reports that the fingering of North Korea as responsible for the attack on the network of Sony Pictures Entertainment was through evidence gathered by National Security Agency surveillance. This includes software taps into networks associated with North Korea’s network warfare and espionage unit, Bureau 121, among others. The actual evidence, however, will likely never see the light of day because of the highly classified nature of how it was obtained.
David Sanger and Martin Fackler of the Times report that the NSA started to ramp up efforts to penetrate North Korea’s networks in 2010 to monitor the growth of Bureau 121 and the rest of the country’s “computer network exploitation” capabilities:
A classified security agency program expanded into an ambitious effort, officials said, to place malware that could track the internal workings of many of the computers and networks used by the North’s hackers, a force that South Korea’s military recently said numbers roughly 6,000 people. Most are commanded by the country’s main intelligence service, called the Reconnaissance General Bureau, and Bureau 121, its secretive hacking unit, with a large outpost in China.
The evidence gathered by the “early warning radar” of software painstakingly hidden to monitor North Korea’s activities proved critical in persuading President Obama to accuse the government of Kim Jong-un of ordering the Sony attack, according to the officials and experts, who spoke on the condition of anonymity about the classified NSA operation.
The NSA’s Tailored Access Office, according to the report, “drilled into the Chinese networks that connect North Korea to the outside world, picked through connections in Malaysia favored by North Korean hackers, and penetrated directly into the North with the help of South Korea and other American allies.” According to NSA documents released by Der Spiegel, some of South Korea’s initial assistance was not voluntary—the NSA secretly exploited South Korea’s existing hacks of North Korea to gain intelligence information. But despite the level of access they gained, according to an unnamed investigator into the Sony Pictures attack, the NSA and other US agencies “couldn’t really understand the severity” of the attack that would be launched against Sony when they began on November 24.
Read on Ars Technica | Comments
The Challenge of Reporting Cyberwar
Journalists face an unprecedented challenge in reporting cyberwars accurately
What’s Involved in Cyber War Games?
What’s involved in testing critical systems?
South Korea Says North Korea Doubled Size of Its “Cyber Forces,” Can Nuke US
A report published by South Korea’s Defense Ministry on December 6 estimates that North Korea has further increased its focus on network and electronic warfare over the last year, doubling the size of its “cyber forces” to 6,000 soldiers. The report also warned that North Korea has made significant advances in its nuclear weapons technology and could now have the capability of threatening the mainland of the United States with a nuclear strike.
The report, the ministry’s 2014 Defense White Paper, is a biennial review of South Korea’s defense policy similar to the US Department of Defense’s Quadrennial Review, intended to define the government’s defense policy. Defense Ministry officials stated in the report that North Korea’s efforts in cyber-warfare and other “asymmetric” capabilities are part of an effort to cause “physical and psychological paralysis inside South Korea such as causing troubles for military operations and national infrastructures.”
The Defense Ministry report also claimed that North Korea had made advances in miniaturization of nuclear warheads, which
would allow them to be mounted more readily on intercontinental ballistic missiles. “The ability to miniaturize nuclear weapons seems to be at an early but significant level and is estimated as having the ability to threaten the US mainland through a long-range missile,” a Defense Ministry spokesperson said in a summary of the report. The assessment is based on estimates of North Korea’s production of highly enriched uranium.
Read on Ars Technica | Comments
Report Says Cyberattacks Originated Inside Iran
A security firm identified Iranian hackers as the source of coordinated attacks against more than 50 targets in 16 countries, many of them corporate and government entities.![]()
Critical networks in US, 15 other nations, completely owned, possibly by Iran
For more than two years, pro-Iranian hackers have penetrated some of the world’s most sensitive computer networks, including those operated by a US-based airline, auto maker, natural gas producer, defense contractor, and military installation, security researchers said.
In many cases, “Operation Cleaver,” as the sustained hacking campaign is being dubbed, has attained the highest levels of system access of targets located in 16 countries total, according to a report published Tuesday by security firm Cylance. Compromised systems in the ongoing attacks include Active Directory domain controllers that store employee login credentials, servers running Microsoft Windows and Linux, routers, switches, and virtual private networks. With more than 50 victims that include airports, hospitals, telecommunications providers, chemical companies, and governments, the Iranian-backed hackers are reported to have extraordinary control over much of the world’s critical infrastructure. Cylance researchers wrote:
Perhaps the most bone-chilling evidence we collected in this campaign was the targeting and compromise of transportation networks and systems such as airlines and airports in South Korea, Saudi Arabia and Pakistan. The level of access seemed ubiquitous: Active Directory domains were fully compromised, along with entire Cisco Edge switches, routers, and internal networking infrastructure. Fully compromised VPN credentials meant their entire remote access infrastructure and supply chain was under the control of the Cleaver team, allowing permanent persistence under compromised credentials. They achieved complete access to airport gates and their security control systems, potentially allowing them to spoof gate credentials. They gained access to PayPal and Go Daddy credentials allowing them to make fraudulent purchases and allow[ing] unfettered access to the victim’s domains. We were witnessed [sic] a shocking amount of access into the deepest parts of these companies and the airports in which they operate.
Tuesday’s 86-page report relies on circumstantial evidence to arrive at the conclusion that the 20 or more hackers participating in Operation Cleaver are backed by Iran’s government. Members take Persian handles such as Salman Ghazikhani and Bahman Mohebbi; they work from numerous Internet domains, IP addresses, and autonomous system numbers registered in Iran; and many of the custom-configured hacking tools they use issue warnings when their external IP addresses trace back to the Middle Eastern country. The infrastructure supporting the vast campaign is too sprawling to be the work of a lone individual or small group; it could only have been sponsored by a nation state.
Read 7 remaining paragraphs | Comments
Bits Blog: Symantec Discovers ‘Regin’ Spy Code Lurking on Computer Networks
Researchers Uncover Government Spy Tool Used to Hack Telecoms and Belgian Cryptographer

Piecing together new information from various researchers, it’s clear the ‘Regin” malware is one of the most sophisticated nation-state spy tools ever found.
The post Researchers Uncover Government Spy Tool Used to Hack Telecoms and Belgian Cryptographer appeared first on WIRED.
![]()
NSA Director: China Can Damage US Power Grid
Soldiers, Spies, Cyberwarriors: ‘@War’ In The Internet Age
“One if by land, two if by sea” wouldn’t work these days — not when your adversary can knock out your power grid with an team of cyberforces. Today’s armies have a new front to monitor.
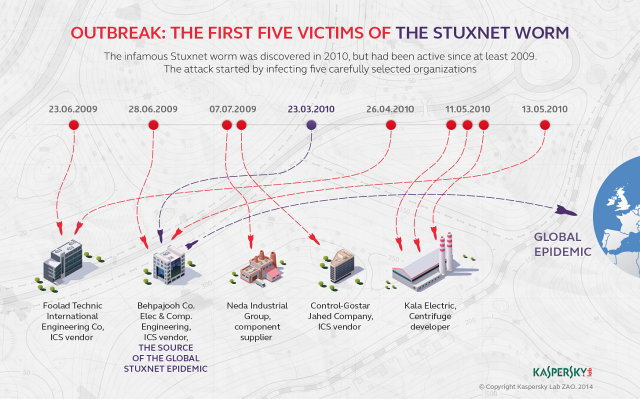
Stuxnet Worm Infected High-Profile Targets before Hitting Iran Nukes
The Stuxnet computer worm that attacked Iran’s nuclear development program was first seeded to a handful of carefully selected targets before finally taking hold in uranium enrichment facilities, according to a book published Tuesday.
The new account, included in Countdown to Zero Day: Stuxnet and the Launch of the World’s First Digital Weapon by Wired reporter Kim Zetter, is at odds with the now-popular narrative that the malware first penetrated Iran’s Natanz enrichment facility and later unexpectedly broke loose to infect hundreds of thousands of other sites across the globe. That earlier account, provided by New York Times journalist David Sanger, characterized the escape outside of Natanz as a programming error that was never intended by engineers in the US and Israel, the two countries Sanger and Zetter said devised and unleashed Stuxnet. According to Zetter, the world’s first known cyber weapon first infected Iranian companies with close ties to Iranian nuclear facilities and only later found its way to Natanz.
“To get their weapon into the plant, the attackers launched an offensive against four companies,” Zetter wrote. “All of the companies were involved in industrial control processing of some sort, either manufacturing products or assembling components or installing industrial control systems. They were likely chosen because they had some connection to Natanz as contractors and provided a gateway through which to pass Stuxnet to Natanz through infected employees.”
Read 6 remaining paragraphs | Comments
An Unprecedented Look at Stuxnet, the World’s First Digital Weapon

In an excerpt from her new book, “Countdown to Zero Day,” WIRED’s Kim Zetter describes the dark path the world’s first digital weapon took to reach its target in Iran.
The post An Unprecedented Look at Stuxnet, the World’s First Digital Weapon appeared first on WIRED.
![]()
Hackers Gather for Cyberwar in an Intense 48-Hour Sim

Locked Shields is among the world’s preeminent cyber attack simulations. For two days, international teams of hackers and system admins play both sides of a war game, simultaneously attacking and defending critical infrastructure. The details are realistic, and the exercises reflect real-world geopolitics. It is a training ground for front-line operators in a rapidly evolving form of warfare in which network administrators at banks, electrical plants and government offices are as crucial to a country’s defense as uniformed troops.
The post Hackers Gather for Cyberwar in an Intense 48-Hour Sim appeared first on WIRED.
![]()
Army Cyber Chief: Let’s Get Closer To Industry- 11 September 2014
11 September 2014- Defense News
Army Cyber Chief: Let’s Get Closer To Industry
ISIS Cyber Capability Judged More ‘Aspirational’ Than Operational- 17 September 2014
17 September 2014- FCW
ISIS cyber capability judged more ‘aspirational’ than operational
Kremlin Wants to ‘Protect Russian Cyberspace from Unpredictable West’- 19 September 2014
19 September 2014- Security Week
Kremlin Wants to ‘Protect Russian Cyberspace from Unpredictable West’
Hackers Penetrated Systems of Key Defense Contractors- 18 September 2014
18 September 2014- Help Net Security
Hackers penetrated systems of key defense contractors
US Naval Academy Works on Accrediting Cyber Major- 8 September 2014
8 September 2014- The Washington Times
US Naval Academy Works on Accrediting Cyber major
North Korea Cyber Warfare Capabilities Exposed- 2 September 2014
2 September 2014- ZDNet
North Korea cyber warfare capabilities exposed