A security firm identified Iranian hackers as the source of coordinated attacks against more than 50 targets in 16 countries, many of them corporate and government entities.![]()
Category Archives: Iran
Critical networks in US, 15 other nations, completely owned, possibly by Iran
For more than two years, pro-Iranian hackers have penetrated some of the world’s most sensitive computer networks, including those operated by a US-based airline, auto maker, natural gas producer, defense contractor, and military installation, security researchers said.
In many cases, “Operation Cleaver,” as the sustained hacking campaign is being dubbed, has attained the highest levels of system access of targets located in 16 countries total, according to a report published Tuesday by security firm Cylance. Compromised systems in the ongoing attacks include Active Directory domain controllers that store employee login credentials, servers running Microsoft Windows and Linux, routers, switches, and virtual private networks. With more than 50 victims that include airports, hospitals, telecommunications providers, chemical companies, and governments, the Iranian-backed hackers are reported to have extraordinary control over much of the world’s critical infrastructure. Cylance researchers wrote:
Perhaps the most bone-chilling evidence we collected in this campaign was the targeting and compromise of transportation networks and systems such as airlines and airports in South Korea, Saudi Arabia and Pakistan. The level of access seemed ubiquitous: Active Directory domains were fully compromised, along with entire Cisco Edge switches, routers, and internal networking infrastructure. Fully compromised VPN credentials meant their entire remote access infrastructure and supply chain was under the control of the Cleaver team, allowing permanent persistence under compromised credentials. They achieved complete access to airport gates and their security control systems, potentially allowing them to spoof gate credentials. They gained access to PayPal and Go Daddy credentials allowing them to make fraudulent purchases and allow[ing] unfettered access to the victim’s domains. We were witnessed [sic] a shocking amount of access into the deepest parts of these companies and the airports in which they operate.
Tuesday’s 86-page report relies on circumstantial evidence to arrive at the conclusion that the 20 or more hackers participating in Operation Cleaver are backed by Iran’s government. Members take Persian handles such as Salman Ghazikhani and Bahman Mohebbi; they work from numerous Internet domains, IP addresses, and autonomous system numbers registered in Iran; and many of the custom-configured hacking tools they use issue warnings when their external IP addresses trace back to the Middle Eastern country. The infrastructure supporting the vast campaign is too sprawling to be the work of a lone individual or small group; it could only have been sponsored by a nation state.
Read 7 remaining paragraphs | Comments
Iran frees ‘Blogfather’ Derakhshan
Iran’s Supreme Leader has pardoned the pioneering Iranian-Canadian blogger Hossein Derakhshan after six years in prison, Iranian media report.
Stuxnet Worm Infected High-Profile Targets before Hitting Iran Nukes
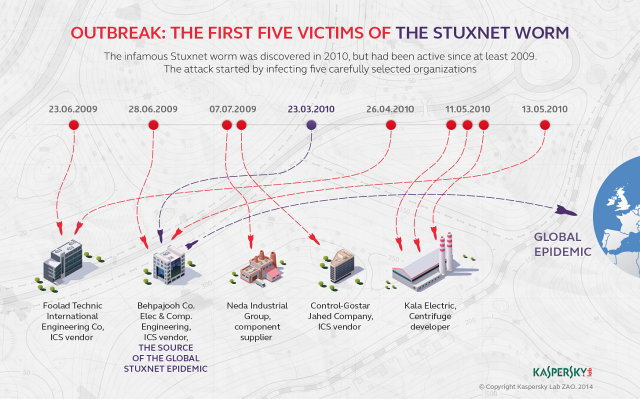
The Stuxnet computer worm that attacked Iran’s nuclear development program was first seeded to a handful of carefully selected targets before finally taking hold in uranium enrichment facilities, according to a book published Tuesday.
The new account, included in Countdown to Zero Day: Stuxnet and the Launch of the World’s First Digital Weapon by Wired reporter Kim Zetter, is at odds with the now-popular narrative that the malware first penetrated Iran’s Natanz enrichment facility and later unexpectedly broke loose to infect hundreds of thousands of other sites across the globe. That earlier account, provided by New York Times journalist David Sanger, characterized the escape outside of Natanz as a programming error that was never intended by engineers in the US and Israel, the two countries Sanger and Zetter said devised and unleashed Stuxnet. According to Zetter, the world’s first known cyber weapon first infected Iranian companies with close ties to Iranian nuclear facilities and only later found its way to Natanz.
“To get their weapon into the plant, the attackers launched an offensive against four companies,” Zetter wrote. “All of the companies were involved in industrial control processing of some sort, either manufacturing products or assembling components or installing industrial control systems. They were likely chosen because they had some connection to Natanz as contractors and provided a gateway through which to pass Stuxnet to Natanz through infected employees.”
Read 6 remaining paragraphs | Comments
An Unprecedented Look at Stuxnet, the World’s First Digital Weapon

In an excerpt from her new book, “Countdown to Zero Day,” WIRED’s Kim Zetter describes the dark path the world’s first digital weapon took to reach its target in Iran.
The post An Unprecedented Look at Stuxnet, the World’s First Digital Weapon appeared first on WIRED.
![]()
Apple Looks to Sell iPhone in Iran
Apple is in preliminary contact with Iranian distributors about possibly selling the iPhone in the country. Iran has 77 million people, but the market is fraught with obstacles.
Iran’s Emergence as a Cyber Power- 20 August 2014
20 August 2014- Strategic Studies Institute
Iran’s Emergence as a Cyber Power
Iranian Hackers ‘Friended’ Four-star U.S. Admiral on Facebook to Steal Data Using Social Media Espionage – May 29, 2014
5/29/2014 – National Post
Iranian hackers ‘friended’ four-star U.S. admiral on Facebook to steal data using social media espionage
Iranian Hackers Targeted Defense Workers and Political Dissidents- 13 May 2014
13 May 2014- Recode
Iranian Hackers Targeted Defense Workers and Political Dissidents
Iranian Hackers Target US Defense Contractors- 13 May 2014
13 May 2014- Threat Post
Iranian Hackers Target US Defense Contractors
The HP Security Research group details Iranian cyber capabilities – February 24, 2014
Iranian Hacking to Test NSA Nominee Michael Rogers – February 18, 2014
2/18/2014 – Wall Street Journal
Iranian Hacking to Test NSA Nominee Michael Rogers