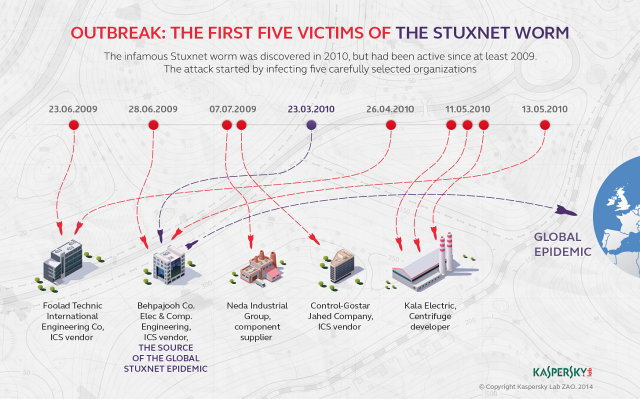
Recent revelations that Uber stored a sensitive database key on a publicly accessible GitHub page generated its share of amazement and outrage. Some Ars readers called for the immediate termination of the employees responsible or for the enactment of new legal penalties for similar blunders in the future.
Left out of the discussion was a point Ars first tried to drive home more than two years ago. To wit, GitHub and other public code repositories are awash with personal credentials posted by tens of thousands, or possibly even millions, of people, some of whom work for extremely sensitive organizations. A case in point are GitHub entries that appear to include everything needed to log into many Secure File Transfer Protocol accounts. One GitHub search revealed almost 269,000 entries like the one pictured above, showing the domain name or IP address, username, and password needed to log in to each account. Similar searches generated almost two million entries for WordPress accounts.
A quick scan of the results shows that many of them represent no security threat at all, since the password fields are blank or the credentials belong to non-existent accounts or accounts that are accessible only to users already connected to the local network. But a mind-numbingly large percentage of the results appear to provide credentials for accounts on production servers. Whether percentage is 33, 25, or even 10, it’s way too high. It wouldn’t be surprising if many of the credentials offered shell accounts that ran with highly privileged administrator rights. To protect the careless, this post won’t reveal the specific search terms used, even though they are extremely easy for readers figure out on their own or to find on Twitter, in blog posts, or in other venues.
Read 3 remaining paragraphs | Comments