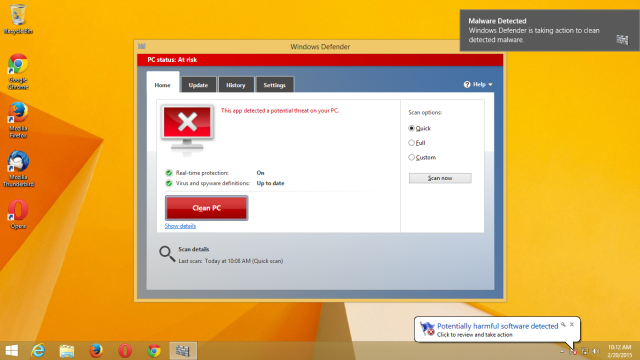
First the good news. Microsoft today released a signature update for Windows Defender, the anti-malware software that’s built in to Windows, to enable it to both detect and remove the Superfish malware that Lenovo installed on some systems.
Defender’s removal process seems to be quite robust, both uninstalling the software and removing the dangerous certificate that Superfish installs. However, it doesn’t appear to clean any contaminated installs of Firefox or Thunderbird; for that, you’ll want to check out our manual removal instructions.
Now the bad news. While Windows Defender is supplied as part of Windows and works well enough, Microsoft gave it some rather strange behavior as a concession to third-party anti-malware vendors. If a third-party anti-malware product is installed, Windows Defender will automatically disable itself. Many Lenovo systems include trial versions of anti-malware software; during the duration of these trials, Windows Defender will be inactive.
Read 2 remaining paragraphs | Comments