Strict regulations will need to be introduced before large drones are allowed to appear in the UK’s skies, pilots association Balpa has said.
Month: October 2014
Verizon’s ‘Perma-Cookie’ Is a Privacy-Killing Machine

Verizon Wireless has been subtly altering the web traffic of its wireless customers for the past two years, inserting a string of about 50 letters, numbers, and characters into data flowing between these customers and the websites they visit. The company—one the country’s largest wireless carriers, providing cell phone service for about 123 million subscribers—calls […]
The post Verizon’s ‘Perma-Cookie’ Is a Privacy-Killing Machine appeared first on WIRED.
![]()
Exposing the History of Hacking
The birth of the hacker sub-culture
Now Everyone Wants to Sell You a Magical Anonymity Router. Choose Wisely

Maintaining your privacy online, like investing in stocks or looking good naked, has become one of those nagging desires that leaves Americans with a surplus of stress and a deficit of facts. So it’s no surprise that a cottage industry of privacy marketers now wants to sell them the solution in a $50 piece of hardware promising internet “anonymity” or “invisibility.” And as with any panacea in a box, the quicker the fix, the more doubt it deserves.
The post Now Everyone Wants to Sell You a Magical Anonymity Router. Choose Wisely appeared first on WIRED.
![]()
Speaker Series – Hubert Yoshida: 23 Oct 2014
Pro-Privacy Senator Wyden on Fighting the NSA From Inside the System

Wyden spoke with WIRED about the difficulties of keeping mum on classified matters, about his public showdown with intelligence chief James Clapper over the NSA’s data collection on Americans, and about the government’s use of zero-day exploits.
The post Pro-Privacy Senator Wyden on Fighting the NSA From Inside the System appeared first on WIRED.
![]()
Mac OS X Yosemite Sends Location, Search Data to Apple
Two steps toward privacy, one step back.
While privacy advocates lauded Apple for the company’s decision to default to encrypting data on its latest mobile operating system, iOS 8, the technology firm faced criticism on Monday after independent researchers discovered that its latest operating system, Mac OS X Yosemite, is configured to send location and search data whenever a user queries Spotlight.
Spotlight is the company’s search feature for Mac OS X. The capability doesn’t just search a user’s computer, though; it also sends information to Apple and Microsoft to return searches from the companies’ services, according to Fix-MacOSX.com.
Read 4 remaining paragraphs | Comments
Chinese Government Launches Man-in-Middle Attack Against iCloud
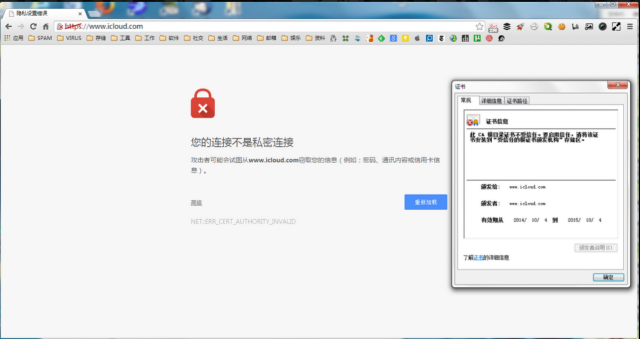
GreatFire.org, a group that monitors censorship by the Chinese government’s national firewall system (often referred to as the “Great Firewall”), reports that China is using the system as part of a man-in-the-middle (MITM) attack on users of Apple’s iCloud service within the country. The attacks come as Apple begins the official rollout of the iPhone 6 and 6 Plus on the Chinese mainland.
The attack, which uses a fake certificate and Domain Name Service address for the iCloud service, is affecting users nationwide in China. The GreatFire.org team speculates that the attack is an effort to help the government circumvent the improved security features of the new phones by compromising their iCloud credentials and allowing the government to gain access to cloud-stored content such as phone backups.
Chinese iCloud users attempting to log in with Firefox and Chrome browsers would have been alerted to the fraudulent certificate. However, those using Mac OS X’s built-in iCloud login or another browser may not have been aware of the rerouting, and their iCloud credentials would have been immediately compromised. Using two-step verification would prevent the hijacking of compromised accounts.
Read 1 remaining paragraphs | Comments
Google Rolling Out New Anti-Piracy Search Algorithm
Google will begin rolling out a change to its search algorithm that the media giant says will “visibly affect” rankings of piracy sites globally.
The Mountain View, California company promised to do this in 2012. But at the time, the Recording Industry Association of America, the Motion Picture Association of America, and others said the changes to its search algorithm had “no demonstrable impact on demoting sites with large amounts of piracy.” Google said the latest global algorithm changes, to roll out this week, will work.
“In August 2012 we first announced that we would downrank sites for which we received a large number of valid DMCA [Digital Millennium Copyright Act] notices,” Google’s senior copyright counsel Katherine Oyama wrote in a Friday blog post. “We’ve now refined the signal in ways we expect to visibly affect the rankings of some of the most notorious sites.”
Read 8 remaining paragraphs | Comments
How to Stop Apple From Snooping on Your OS X Yosemite Searches

Apple’s latest operating system OS X Yosemite pushes the limits of data collection tolerance: its desktop search tool Spotlight uploads your search terms in real time to Apple’s remote servers, by default. Fortunately for Apple’s angry users, however, this is one privacy invasion that’s easy to cut short.
The post How to Stop Apple From Snooping on Your OS X Yosemite Searches appeared first on WIRED.
![]()



You must be logged in to post a comment.